Thermostatic Radiator Valve Head Thermostatic Radiator Valve Head Ningbo Safewell Plumbing Co., Ltd. , https://www.safewellbrass.com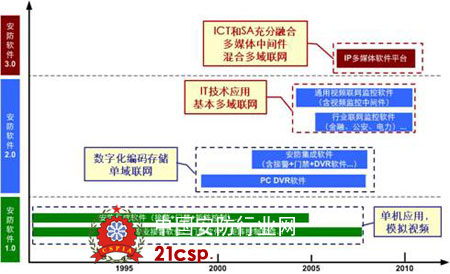 First, the development history of security software Since the 1990s, with the rapid development of computer, communications, control and multimedia technology, security software as a key component of the security system, in the security system, digital, network, intelligent development Under the general trend, its importance has been increasingly valued by customers, and it has also been greatly developed.
First, the development history of security software Since the 1990s, with the rapid development of computer, communications, control and multimedia technology, security software as a key component of the security system, in the security system, digital, network, intelligent development Under the general trend, its importance has been increasingly valued by customers, and it has also been greatly developed.
The management scope of security software includes video surveillance, intrusion prevention, access control, and environmental monitoring. In the early 1990s, security software was mainly sold using the hardware of an integrated security system, such as matrix control software for video surveillance matrix. The access control management software of the access control system and the alarm management software of the professional intrusion prevention system are more of the supporting and matching roles. The main suppliers are all security system hardware vendors. The mainstream hardware manufacturers in the country generally provide hardware. The free matching management software, the security software function of this period is simple and simple, there are few participating companies, and their value and importance are not fully valued.
In the mid to late 1990s, with the rapid development of the smart building market, combined with the requirements of the IBMS intelligent building management system, there were professional firms on the market that could provide integrated management of major security systems such as matrix control, alarm alarm and access control management. The first generation of security integrated management software, at the same time through the OPC server and other common interfaces, can also achieve linkage collaboration with the BA Building Control System, and jointly build an intelligent building management platform, this time as the most important part of the security system, video surveillance system It also mainly uses the full analog architecture of analog matrix plus analog video recorders. The companies that can provide such software are mainly several major international security companies and their supporting manufacturers. In some high-end intelligent buildings, the first generation of security integration software has been initially applied, but its overall value and importance in China are still not Recognized universally, until today, most smart buildings still use separate software provided by various security subsystems.
It is necessary to pay attention to the fact that in the mid to late 1990s, China’s operator field (at that time called the Ministry of Posts and Telecommunications) proposed the construction of a monitoring and control system for telecommunication engine room power and environment, and a user unit based on the telecommunications DDN private network and network construction network monitoring. The power, environment, alarm, and access control systems in the telecommunications room are managed in a unified manner based on a set of software.
By the end of the 1990s, the telecommunications sector first proposed the digitalization of computer room images for networked monitoring and the need for network monitoring. For the first time, a large-scale PC-based DVR product based on hardware-level video compression acquisition cards was used in computer room monitoring. There are not many units participating in engine room monitoring. Strictly speaking, the engine room monitoring system does not belong to the category of security monitoring software. At that time, it did not attract the attention of the whole industry, but the technologies therein are similar, and many of these companies and their Employees have become backbone enterprises and backbone forces in the development of domestic network security monitoring software.
In the last years of the end of the last century, security software was applied in the industry in a large scale and received universal attention. The opportunity was the introduction of hardware video compression cards, and the development of universal DVR digital hard disk recorders based on hardware video compression cards. The PC-type DVR with video compression card and DVR hard disk recorder software began to be applied in the bank teller video transformation field, gradually replacing the traditional analog video recorder, and promoting the transition from analog surveillance to digital surveillance in video surveillance. Due to the low threshold of DVR software development, a large number of local companies have the ability to enter the development of security monitoring core products for the first time, breaking the monopoly position of Japanese and Korean companies over the years in video surveillance products. Until now, China’s hard drives VCR products have occupied a large share in the international market and are the first core security products recognized by foreign markets as a whole. During this period, many professional PC DVR software development units with higher market share have emerged, such as Tianshi, Goldeneye, Dragon (Longview), Jienuo, etc. These companies have also become participants in today's online video software development.
In the 21st century, under the general trend of rapid development of digital video surveillance, the development of security software presents a flourishing trend. There are four major development directions that can be seen:
1) The traditional intelligent building security integration software began to integrate digital image monitoring into its software, such as the United States LELEN integrates DVR software and access control alarm software, the domestic cluster software will integrate professional intrusion alarms and DVR, access control software;
2) The original security hardware supporting software began to support simple security system linkage integration, such as Israel DSS access control software and DVR digital monitoring software integration linkage, some DVR digital monitoring software can achieve professional intrusion alarm host management;
3) The original computer room network monitoring software development companies and PC-DVR software vendors began to launch general-purpose security network management software mainly for video surveillance, such as ZTE, mutual aid, etc., in the computer room network, banking network, and public security network monitoring. Get a preliminary application;
4) Some development companies that develop PC-DVRs, computer room monitoring software, or even industrial control SCDA software combine the special requirements of users in certain industries. Through custom development, the application of universal video network monitoring software will be applied to Ping An Engineering, financial off-site storage, and interrogation. , Enterprise production monitoring, scenic monitoring and propaganda, remote insurance damage and even nursery baby care and other fields, and some even do not belong to the field of security, but essentially belong to security software derivatives.
The security software before the end of the 1990s can be called security software 1.0. Its main feature is that it is mostly a single system software matching the security hardware. It has a single function, low integration capability, does not support digital image monitoring technology, does not support large Scale networking.
With the application of digital image coding technology in the field of security, the emergence of PC-style DVR software, from the end of the last century, security software into the 2.0 era, its main feature is the use of digital encoding technology for image storage and networking, security and other applications and image monitoring technology Began to integrate and integrate, from the perspective of the management software itself, from the product architecture and functional design can basically meet the security system integration networking needs. After entering this era, security software began to be applied on a large scale and was valued by customers. In particular, it has become a core component of the entire system in networked monitoring projects such as finance, public security, and telecom room, and a large number of security software companies have emerged. Most of them are derived from the development of PC-DVR software, and some are from traditional security integration software, computer room monitoring software, or even industrial control SCADA software companies.
Some companies in the development of security 2.0 software have already been in the leading position in the development of security software. Their design is not only to meet the needs of customers for the function, but to develop from the perspective of the overall design of the upper application software. Integrated software, using mature technologies in IT software development, including SOA, J2EE/. Standard IT software development technologies such as NET middleware technology, WEB2.0 technology, object-oriented development, LDAP, single sign-on, etc., have a great deal of flexibility in terms of software, scalability, and development technology. The promotion has introduced the universal video network monitoring platform software, and based on this industry-oriented network monitoring software.
Second, the security software middleware proposed Digital video surveillance software is the development of security software, the most dynamic and the most widely used software, with the bank network monitoring, security engineering network monitoring and power, energy, environmental protection and other industries for video surveillance With the continuous increase in networking requirements, the environment and requirements faced by security software have become increasingly complex. The original stand-alone PC-DVR software has been unable to meet the needs of such customers.
Network monitoring has become the biggest driving force for the continuous development of security software. In the online video surveillance market, the network extends from LAN to VPN private network, INTERNET and other wide-area networking, and the number of users from single-machine access is not a large amount of concurrent access. The video storage requirements are getting higher and higher, the number of days of storage and capacity are increasing, and the types of devices accessed from the front end are also extended from single-brand PC-DVR to various brands of PC-DVRs, embedded DVRs, DVS video servers, and video codecs. Equipment, some customers also require the management of intrusion alarms and access control systems.
In the face of market demand, new software forms such as streaming media servers, network storage servers, device access servers, proxy servers, WEB servers, GIS servers, and alarm processing servers have emerged in an endless stream. At the same time, various issues have arisen as a result of market prosperity. Feasible industry standards, product quality varies greatly, and even between vendors and even their own products can not be interconnected, can not be stable and reliable composition of the monitoring system to accommodate different manufacturers of products;
Due to the high technical barriers to software development of large-scale networked monitoring systems, few companies have the ability to develop high-quality system-level monitoring software. In this context, many small companies lacking strength have been eliminated. The digital surveillance equipment manufacturers have proposed a new, standardized and open network monitoring software development model in order to reduce the software technology threshold for security software developers to develop network management of their equipment and promote the development and development of the network video surveillance market. - Based on the "security software middleware" development model;
Borrowing from the mature middleware open model in the field of IT software, security software middleware is located between security application software and operating system hardware. It can run on multiple hardware and OS platforms, supports distributed computing, and provides cross-network, hardware, and OS platforms. The transparency of the application or service interaction, support for standard protocols and interfaces, to meet the needs of a large number of video surveillance applications, in line with the development direction of the security industry software development, in line with the IT industry's software development direction, the specific product composition includes: 1) DVR/DVS Device Agents; 2) Streaming Media Forwarding; 3) Permission Verification; 4) Playback and Video Walls; 5) Database; 6) Firewall Traversal; 7) Network Storage; 8) Electronic Map; 9) Messaging, etc.
The proposal of the middleware can indeed greatly reduce the difficulty for software developers to develop a set of networked video surveillance software. However, in practical applications, this type of middleware mainly targets only the middleware vendor's own front-end DVR/DVS. Equipment, and require software developers have a certain degree of software architecture design capabilities, and the actual project in the front-end management equipment is often more than one brand, a real software company with a certain strength or choose based on different manufacturers front-end DVR / DVS to develop network monitoring software, The lack of strength of software vendors due to market competition and inferior disadvantages, it is difficult to obtain sufficient competitive advantage based on the development of the middleware, coupled with the lack of middleware platforms for security alarms, access control and other systems, so In the end, it did not gain universal recognition in the market and did not become a mainstream product development form.
There are also some software vendors who, based on their security integrated networking software, provide integrators with personalized customization functions such as function cutting, interface layout customization, interface skin replacement, and electronic map design, and also define their software as security software. The middleware platform, in a strict sense, can only be defined as a security configuration software with a certain degree of flexibility in customization because third parties cannot use the platform to develop more advanced applications. Middleware.
Third, the current security software integration platform and security software middleware main problems Currently, the entire security monitoring system has entered the era of network monitoring, whether it is video surveillance codec, alarm access, access control or shared storage and network All of them began to present the trend of networked development with IP as the main feature. The rapid growth of network monitoring requirements in various industries puts forward new requirements for security software. How to achieve cross-regional networking with the simplest possible architecture and highest efficiency The viewing, control, storage, management, and use of basic services within the global scope of the surveillance system have become issues that must be considered by every security software vendor.
During this period, whether it is security software 1.0, 2.0 or security software middleware, due to the limitations of the development unit's capabilities, it is difficult to get involved in the development of various aspects of the network monitoring system, its design ideas focus on the various security systems to consider security software The design focuses on the security software itself, rather than on the network monitoring requirements for the integration optimization of the entire security system.
In fact, when the scope of network monitoring continues to expand, massive video access and video storage rely on traditional software design already has some insurmountable bottlenecks. From the perspective of traditional software vendors, solving problems can only proceed from the software itself, and cannot The overall architecture of network monitoring perspective to consider optimization. The end result is heterogeneous, non-standard hardware, different vendor storage, networking plus security software platforms, and software that can be used to knead these hardware. It can be said that integration is also a piece of patchwork. In the traditional security software eco-environment, software can only passively adapt to hardware, trying to build a bridge between the hardware and software in the network monitoring environment, and can not optimize the relevant components of network monitoring from the perspective of the entire network monitoring and control. These components include front-end, storage, and embedded software on network devices. Therefore, components such as streaming media server, network transfer server, and device proxy server appear to implement real-time and storage video streaming processing and signaling processing. In the face of massive multimedia information management and storage requirements, these devices are clustered and load balanced. The reliability design of fault switching and the performance bottleneck of its overall architecture have become an important factor hindering the development of network monitoring.
Another trend is that one of the characteristics of network monitoring is the exponential increase in network bandwidth and mass storage data capacity. Currently, both security monitoring and other areas of monitoring management have begun to show multimedia features through video and audio codec technologies. Applications, using converged video surveillance, video conferencing, voice communications, instant messaging, video information distribution, and other multimedia means to achieve improved management and control efficiency. At the same time, a large amount of multimedia data needs to be saved and searched on-demand. These multimedia data fusion and Mass storage data integrated management technology is not fully grasped by general security software vendors. Facing the rapid increase in demand for multimedia management and monitoring in the entire industry, traditional security software vendors and integrators are facing unprecedented challenges. On the one hand, they need to remain in the local market. The profitability, on the other hand, also needs to invest a lot of R&D resources to meet the growing demand for the reliability, stability, and multimedia management of the massive monitoring and management market in the network monitoring market, due to the new components in network monitoring such as network, multimedia, and storage. The accumulation of lack of technique, in the current economic environment, how to achieve profitability of these enterprises have become the problem of the current urgent need to consider.
Fourth, network monitoring promotes security software to enter the 3.0 era The rapid development of the security monitoring market, as well as its problems in the development of network monitoring, so many large-scale network IT companies see the opportunity to use its richness in the network, storage, multimedia fields Accumulated experience, from the perspective of the overall structure of the security monitoring system for a new review and planning, including the international CISCO, IBM, Nokia Siemens and domestic H3C, Huawei, ZTE have begun to intervene in this market. In 2006, H3C took the lead in redesigning and planning the security monitoring system based on its years of IP network, IP storage, IP multimedia and service software platform product development experience in the industry market, and put forward the overall architecture perspective of network monitoring. The integration of the four components of the network, storage, video codec and management software is designed.
The greatest feature of H3C's network monitoring and control solution is that it can optimize the design of its switches, IPSAN disks and codec embedded software and management software for the needs of network monitoring, and not just rely on management software to adapt hardware. This also implements many functions that traditional security software cannot achieve. This includes the ability to encode encoded video storage data directly into the IP SAN storage array through the management platform's cooperating codec embedded software, eliminating the need for traditional network monitoring of streaming media. Store software; use the multicast software embedded in the network switch to optimize, realize the access based on the massive video data of the switch multicast protocol, without the traditional network monitoring streaming media server; use the flow control frame software optimization of the encoder and switch to realize the connection The access efficiency of the incoming stream to the switch is close to 100%, which exceeds the utilization rate of the traditional network monitoring switch by more than 50%. At the same time, the network storage capacity and the live stream delay are optimized and improved.
For networked requirements, the system's optimization and integration of network security software, including all network monitoring components (switches, storage, codecs) embedded software, is an important indicator of security software 3.0, which is also IC network communications The first integration of IT information technology and SA security automation technology. Security Software 3.0 implements a redesigned optimization of the network monitoring system from the perspective of the overall architecture, making the network monitoring application simpler, more efficient, and more reliable. It can easily realize the overall view, control, storage, management and use of services. Instead of just relying on the management software itself to manage a pile of equipment.
V. IMOS and security software 3.0
In response to the trend of management and multimedia development in the entire industry, in 2009, H3C launched the IMOS (IP Multimedia Operating System), which is based on the requirements of network monitoring and multimedia convergence management. IMOS is H3C IP monitoring and video. The software platform common to multimedia products such as conferences is essentially a middleware platform including multimedia integrated monitoring, conference communication, voice communication, and information release. It can support management platform components and can also support all multimedia codec terminals. The equipment and all components are integrated and optimized for the network monitoring service, which can conveniently support the global view, control, storage, management and use of various cross-regional network monitoring systems. At the same time, optimizing integration design for multimedia integrated management applications is another important feature of security software 3.0, and it is also an inevitable requirement for the development of multimedia management and control applications in the industry.
Not only all H3C products, all software vendors in the field of multimedia monitoring and communications can quickly develop various multimedia integrated application platforms through the platform. The introduction of the platform will help reduce the development cost of the original application software vendors, and monitor The optimization of industrial value chain plays a very good role in promoting.
IMOS platform positioning and middleware platform, and traditional security software middleware is different:
1) As the core support platform for security software 3.0, not only for the upper management platform, it has optimized support for codecs, network storage, and network transmission and switching in network monitoring, and can easily support the overall situation of various cross-regional network monitoring systems. See, control, deposit, manage and use business needs.
2) As an open platform, its management equipment is not limited to H3C's own front-end equipment. Besides being able to manage other digital image front-ends, it can also manage security alarms, access control, SCADA and other equipment through the general I/O engine;
3) Its openness is not limited to the top-level applications. Because of its modularity and platform design, SOA's open architecture is followed at all levels of the software, providing much more secondary development than traditional security software middleware. means;
4) As it is a multimedia integrated application platform and supports almost all international standards and SIP signaling standards in the multimedia field, it can conveniently implement multimedia monitoring systems and video conferencing, video on demand, live video, voice communications, instant messaging, and multimedia information publishing. With the integration of application systems, the future monitoring experience and collaborative alarm processing methods are greatly enriched, and the application of multimedia management in the industry has become more handy;
5) In the face of the demand for multimedia storage management for mass storage data applications, IMOS has integrated the MAS (Media Access Service) multimedia storage architecture, and has analyzed in detail multimedia data and multimedia system features under different application scenarios. Storage data management is divided into streaming media application layer, media data direct access interface layer, data organization layer, storage resource shielding layer and physical resource layer, and is proposed to be more suitable for multimedia data features and access characteristics in video surveillance and conference multimedia systems. "Virtual multimedia file system" establishes a data relationship matrix between multimedia storage data and intelligent feature data, which is suitable for various storage media, and at the same time, it can conveniently realize the life cycle management of storage data, making the application and management efficiency of multimedia data more efficient. Has been greatly improved.
VI. Concluding remarks It can be predicted that the growing demand for network monitoring will promote the emergence and development of security software 3.0. At the same time, the ecological environment of the entire security industry will likely undergo major changes. Even a platform manufacturer in the 3.0 era cannot Quickly meet the customization requirements of all industries, the other way out of the original 2.0 era security software is to shift to the industry application software development or software integration market. Based on the market-based game, IT companies including H3C began to move from a relatively closed market strategy to a fully cooperative market strategy. H3C positioned itself to provide high-quality, high-reliability, and standardized multimedia application platforms based on industry applications. The partners have flexible and rapid development capabilities in customizing software in the industry and provide customers with complete solutions.